What Makes SOC Assessment Services and Reports Essential?
SOC Assessment Services
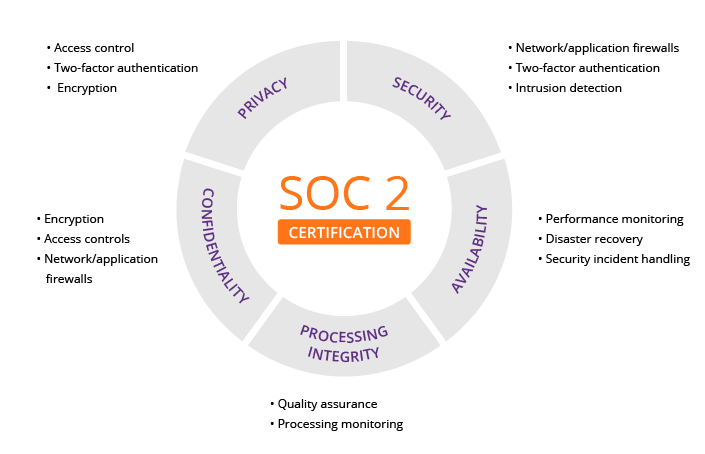
The cybersecurity threats are increasing these days and companies are worried about how to keep then at bay. The data breaches in any industrial sector have become a common incident and it is imperative to bring in tighter security measures to save sensitive customer data from stealing and avoid damages. Service Organization Controls (SOC) help monitor and analyze any business data theft or security posture and a cybersecurity team uses various processes and technological solutions to track and stall them.
With the SOC, you find a systematic framework that offers solutions to safeguard customer data, as well as the brand. The certified public accountant (CPA), which has framed the controls administers them and help companies haveSOC assessments and reports.With these, they can assure safety of their card transactions and build trust, as well as confidence with...







