What Makes SOC Assessment Services and Reports Essential?
SOC Assessment Services
The cybersecurity threats are increasing these days and companies are worried about how to keep then at bay. The data breaches in any industrial sector have become a common incident and it is imperative to bring in tighter security measures to save sensitive customer data from stealing and avoid damages. Service Organization Controls (SOC) help monitor and analyze any business data theft or security posture and a cybersecurity team uses various processes and technological solutions to track and stall them.
With the SOC, you find a systematic framework that offers solutions to safeguard customer data, as well as the brand. The certified public accountant (CPA), which has framed the controls administers them and help companies haveSOC assessments and reports.With these, they can assure safety of their card transactions and build trust, as well as confidence with their customers.
Know the Criteria on Which SOC Assessment Services Are Offered
As for the SOC for information security, CPA has devised it on two distinctive criteria and they are:
Descriptive Criteria: The criteria focus on the effective security controls within a company’s present risk management program and are given in the general narrative descriptions to help facilitate baseline reading.
Control Criteria: With the control criteria, an organization can compare its descriptive data and determine to what extent it has met those requirements.
The information about the effective cybersecurity risk management measures a company has adopted need to be provided irrespective of the control criteria it has chosen. A certified CPA enterprise can evaluate and conduct an SOC compliance assessmentofa company’s cybersecurity health using the information related to control criteria.The security operations of the SOC is the responsibility of the cybersecurity engineers, as well as analysts and they work in confluence with the incident response team of the company to manage any security lapses and build trust in customers.
Know the Different Types of SOC Audit Reports
The SOC reports are classified based on the service usage and the common ones are:
SOC 1 Report
Where your outsourced services have an influence on the internal control over financial reporting (ICFR), you require the SOC 1 report. As for a network monitoring services, data center and payroll processing related businesses, the SOC 1 audit reportis required to show that they meet the requirements through the service they provide.
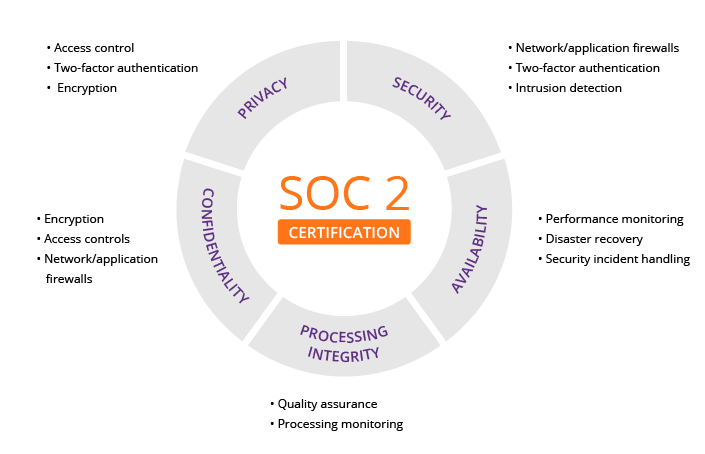
SOC 2 Report
The report is meant for those companies that focus on the Trust Services Criteria (TSC), which are Availability, Confidentiality, Security, Processing Integrity and Privacy. With it, the user entity is educated about the processes that influences the principles mentioned above. The security controls that are followed, disregarded or added are based on how the data provider requires.
SOC 3 Report
This report is a short one and is meant for general audience. Distributed freely, it meets the criteria of the SOC 2 report.
You need to understand the values of different SOC reports and look for the best SOC assessments services that are effectiveness enough to safeguard the security of the system controls in place.